Visual NAND Reconstructor 2.0 update
Dear Friends!
We are getting more and more requests from our users to develop technology or tool for data recovery and forensics of broken smartphones. And this is obvious trend: nowadays people around the world store more and more vital data on the portable gadgets such a smartphones, tables, etc. As our company keeps up with the times, now our users get ability to use VISUAL NAND RECONSTRUCTOR for data retrieval from any broken device based on Android. In a couple with smartphone adapter kit this is unique solution on the market.
Here are new features:
ANDROID DATA EXTRACTOR
Android Data Extractor is an advanced Forensic and Data Recovery platform and part of VNR that helps to retrieve information from memory chips of broken Android smartphones.
Here’s what you can extract with current version of Android Data Extractor:
– Contacts
– Messages: all sms and mms with their attachments
Dynamic interface of data representation with it’s flexible functionality gives you ability to find required information very fast.
Use our sorting, smart filtering and multilevel grouping options to create your own view of the retrieved information.
And finally use our embeded reporting system to export all recovered data to .xlsx files. It will transition all your settings such as sorting, filtering and grouping conditions that you applied in VNR.
Just download sample report of contacts and messages to estimate its flexibility.
Quick video guide for Android Data Extractor
- Contacts
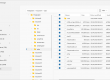
Extract all contacts from Android mobile device very easy and fast.
In the current version you can extract all contacts from Phonebook.
Work with contacts in two modes – short and detailed.
– For every contact in short view you can see the most important information such as name, phones, e-mails, last contacted
time, number of calls, account and source which contact belongs to and also flags of was this contact favorite or deleted.
Very compact and informative data displaying allows you to notice most interesting contacts in a moment.
– To get a very detailed information you need to press toggle button “Show/Hide detailed information”.
There’s a huge amount of information available – photo, addresses, organization data, events, notes, group, website, nickname, relations etc.
- Messages
Get all sms and mms from Android mobile device in a few seconds.
At first sight you can see the maximum of information:
– type of message
– folder it belongs to
– timestamp, parties, body and source of the message
– flags (whether the message deleted or read)
Every mms has attachments which you can see in detailed view by pressing toggle button “Show/Hide attachments”.
Instant access to the most interesting messages with use of filters and grouping.
eMMC IMAGE EXTRACTION MODULE WITH SHADOW COPY ALGORITHMS
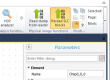
This is a long expected and very efficient addition to the VNR Smartphone kit. It helps to extract data from working and unstable eMMC chips. It was very inconvenient to use hex viewers and other utilities for eMMC physical image extraction because they don’t have a simple way to select and clone the data partition only. There are situation when you begin to extract physical image out of eMMC chip and it fails at one point so you have to reconnect device and extract image again from scratch. Moreover, user’s data partition is normally shifted from beginning by system partitions (sometimes 20-40% of dump).
We solved this problem too with two new elements of VNR which must be connected together – eMMC extraction module and Shadow copy element.
Quick video guide for eMMC and Shadow Copy elements
- eMMC element
eMMC element allows to use externally connected adapter with memory chip (or any other external device) as an image source.
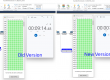
In case if chip is unstable and fails to read data just reconnect adapter and it’ll be automatically connected again. Moreover we save information about read/unread/bad sectors to the map if you use Shadow Copy element. It helps to continue physical image extraction from the point where it failed. The sector that was extracted will never be read again (until you clear the map).
It’s fastest, efficient and safiest possible way to extract physical image out of eMMC memory chips.
- Shadow copy element
Shadow copy element is a real-time buffer for the data that you read out of eMMC chip and an image file container.
You can observe the file system and files through Shadow Copy element without having to image chip first. All sectors you get access to will be READ ONCE and stored im image with mark in map.
When you open file system viewer on Shadow copy element it takes a while to image metadata automatically and show you partition layout and file systems afterwards.
You can selectively image any file, folder or partition you need. Allocated (actual files) or Unallocated space (deleted data) extraction. Extract allocated or anallocated space only on the selected partition. The fragments of extracted data will be shown on the map of Shadow Copy element so you can analyze physical data allocation.
This mode is supported for FAT, NTFS, Ext file systems in the current version. A new unique option to separately extract and compress (remove gaps between fragments) chunks of unallocated space is supported for mentioned file systems.
VISUAL NAND RECONSTRUCTOR PLATFORM IMPROVEMENTS
- WM Partition support (Windows Phone 7.x)
- Automatic search of partition layout schemes and partitions of all supported file systems.
- Support of GPT for 512,1024,2028,4096,8192,16384 bytes sector size
- BCH reread option has been modified with new detailed log
- New NAND commander
- New SET FEATURE/GET FEATURE command for LUNs (0xD4, 0xD5) of NAND chips
- Extended support of ONFI and JESD page decoding
New NAND chips
- 2C64403CA9 29F128G08CFEFB
- 2C48044685 FTL62AP-16G
- 2C64643CA5 4SD22NW553
- 2C646456A5 FxxL94C61KDBABWP
- 2CA4E554A9 PF574-10AL
- 45B394A5E6 SDTNKGHSM-8192
- 45C595A5EA SDTNKHHSM-16384
- 45C799C3AA SDTNLMBHSM-4096
- 98DE989272 RT64G08UCT1-53
- 98DE989272 CA6GL1450D4
- 983A95937A TH58TEG9DDJBA89
- 983A95937A TH58TEGBDDKTA20
- 983A95937A TU89G5LAPA
- 983A999276 microSD Kingston
- 983AA4937A TA17G1LB
- 983AA89276 HVNJ0F8
- 983AA89276 Monolith
- 983AA89276 TC58TE37JDKTA03
- 983C95937A FA64B08UCT1
- 983C95937A FA64B08UCT1-FC
- AD3A18A361 DET0128GWD8HGT5
- ADDE94EB74 D27UCG8T2BYR
- EC3CE9DE88 THGSTMP-1Q06-T1421
- 454CA8A276 mSD
- 45D5843272 mSD
- 983C95937A SDXC Kingston
- 9875A5BA20 SDTNGAHE0-256
- ADD7942544 HY27UDG8VEMYR
- 2CA4E554A9 MT29F1T08CUECBH8
- 2CAC901556 PF226
- 453A949376 05446 064G
- 454C999276 SDTNPNAHEM-016G
- 45DEA8827A Unknown
- 8984643CA9 Unknown
- 983A98A376 FD32B08UCT1-FA
- 983AA89276 Monolith
- 983C95937A FA64B08UCT1-FC
- ADE794DA74 H27QDG8VEBIR-BCB
- EC79A5C0EC K9K1G08U0M
- 2CBC905554 JW391
- 454C95937A monoSD
- 45DE98A272 SDTNSCAMA-008G
- ADBA805500 H8BCS0SI0MAP
- ADDC8015AD HY27UG084G2M
- EC78A5C0EC KAG004003M
- ECBC005554 KA1000012M-BJTT
- 2C646456A5 MT29F64G08CBEFBWP
- 20BC105554 NANDCBR4N9
- 89682446A9 JS29F64G08CCMD1
New scramblers (XOR keys)
- AUnoname_(2k_64p)_F96879.xor
- CBM2098E(16k_128p)_7421A0.xor
- CBM2098E(16k_128p)_7421A0_v1.xor
- EN3257LTQAB(18256b_128p)_4C912A.xor
- IS817(16k_512p)_3C5811.xor
- IS817(17664b_512p_1094_32_xoredSA)_3C5811.xor
- IS817(17664_256p_spare)_405805.xor
- IS902_v1(4k_1p)_BBB928.xor
- IS903(16k_512p)_3C4691_v2.xor
- IS903(16k_512p)_3C4691_v3.xor
- IS903(17600b_512p_1094_30_xoredSA)_3C4691_v3.xor
- IS903(17664_512_spare)_03F085.xor
- IS903(8k_128p)_3C4691.xor
- IS916(4k_256p)_3E092F.xor
- IS916(8k_192p)_08C3B9.xor
- IS916(9216b_192p_1146_24_xoredSA)_08C3B9.xor
- IS917(16k_512p)_3C5811.xor
- IS917(17664b_512p_1094_32_xoredSA)_3C5811.xor
- IT1176E-48B(9216b_258p_580_572_xoredSA_ECC)_988EE1.xor
- MicroSD(8k_8p)_988EE1.xor
- MicroSD(9216b_8p_572_576_572_xoredSA)_988EE1.xor
- PS_monolith(8k_192p)_3A0920.xor
- Sandisk_20-82-00270-1(17664_16p_14_2048_146_xoredSA)_C634C7.xor
- Sandisk_monoSD1(17664k_16p)_7634C3.xor
- SK6617(8k_1p)_7C7CF8F8_v2.xor
- SK6617ABSNE(8k_256p)_7C7CF8F8_v1.xor
- SM2236GAC(4k_128p)_77183F.xor
- SM2236GAC(4k_128p)_8EE645.xor
- SM2685BA(8k_516p)_4C912A_BC.xor
- SM2685BX(8k_256p)_4C912A.xor
- SM2702ABA(8k_128p)_F60234.xor
- SM2702FEA(8832b_128p_1100_31_xoredSA)_F60034.xor
- SM2702FEA(8k_128p)_F60034.xor
- SM2703AA(16k_256p)_17FE70.xor
- SM2703AA(17664b_128p_1094_31_xoredSA)_00F602.xor
- SM2703AA(18048b_128p_1102_31_SA)_00F602_BC.xor
- SM2703AA(18048b_256p_1126_31_xoredSA)_17FE70.xor
- SM2703AA(8704b_128p_1084_31_xoredSA)_17FE70.xor
- SM2703AA(8k_128p)_17FE70.xor
- SM3255Q(4k_128p)_FFFFFF_FFF9FF_v2.xor
- SM3257(8k_256p)_monolith_4C912A.xor
- SM3257(9216b_256p_1148_27_xoredSA)_monolith_4C912A.xor
- SM3257LAC(16k_64p)_D7AF47.xor
- SM3267L(8k_256p)_7F6090.xor
- SM_gluedSD(12k_512p)_D7AF47.xor
- SSS6690U1-N8C(8k_192p)_988EE1.xor
- SSS6691(8640b_256p_1070_xoredSA_ECC)_809E9C.xor
- SSS6695(17664b_256p_1098_xoredSA_ECC)_809E9C.xor
- SSS6695(18048b_256p_1098_xoredSA_ECC)_809E9C.xor
- SSS6697(8k_258p)_C20DC3.xor
- SSS6697(9216b_258p_1140_xoredSA_ECC)_C2C20D0D.xor
- SSS6698(9216b_258p_1140_xoredSA_ECC)_C20DC3.xor
- TC58NC6621G6F(8832b_256p_1070_xoredSA_ECC)_809E9C.xor
- TC58NC6623G6F(8k_258p)_B57AB4_v2.xor
- TC58NC6623G6F(8k_258p)_C20DC3.xor
New monolithic chip pinouts






New ECC
- AU6986_4320(ecc20b)
- AU_blob_2112(ecc30b)
- CBM2098E_18048(ecc604bit)
- CBM2098_9216(ecc116b)
- EN2683B BA_(ecc23b)_4187
- iRiverE300_8640(ecc20b)
- PS2251-33-6_8624(ecc42)
- PS8035-0_9216(ecc76b)
- PS8039-0_17664(ecc74b)
- PS8210-Q_17635_16(ecc74b)
- PS_MicroSD_9216(ecc120b)
- Sandisk monoSD_17663(ecc146b)
- Sandisk_mSD_8640(ecc98)
- SD_noname_8832(ecc77b)
- SK_monolithUFD_18432(ecc114b)
- SM2703AA_18048(ecc102b)
- SM3257L-AC_18336(ecc120)
- SM_gluedSD_13631(ecc112b)
- SS6690_8576(ecc42b)
- SSS6691_8640(ecc42b)
- SSS6695_17664(ecc70b)
- SSS6698_9216(ecc112b)
Fixed bugs
- Folder structure creation error for Ext and HFS+(X)
- Object size error in Ext
- File System Viewer speed is significantly improved, especially for folders with huge amount of files
- Read ID errors
- Many small bugs have been fixed
And all together this is Visual Nand Reconstructor 2.0!
This essential update is available for all users with Premium Support subscription. To check your subscription status or extend it, please send a request to sales@rusolut.com
VNR – your data has never been so close to you!
Your ruSolut Team